Re adversarial interoperability - just figured out a fun approach. Most devices can share their screen over Miracast / AirPlay / something similar (last resort is HDMI cable). Most devices can also receive input from Bluetooth devices (alternatively, through USB cable). So as an alternative to accessibility APIs (or X11, or WinAPI input injection), one might set up another device that would spoof a Miracast display, a bluetooth mouse & a bluetooth keyboard. Such reflector could be implemented in a very cheap form factor (like a tiny ESP32) and allows another app on the original device to effectively bypass all access controls that the OS-es (especially mobile) impose.
It's not a security vulnerability per-se, since it requires the device owner to cooperate - just an interesting way to interop.
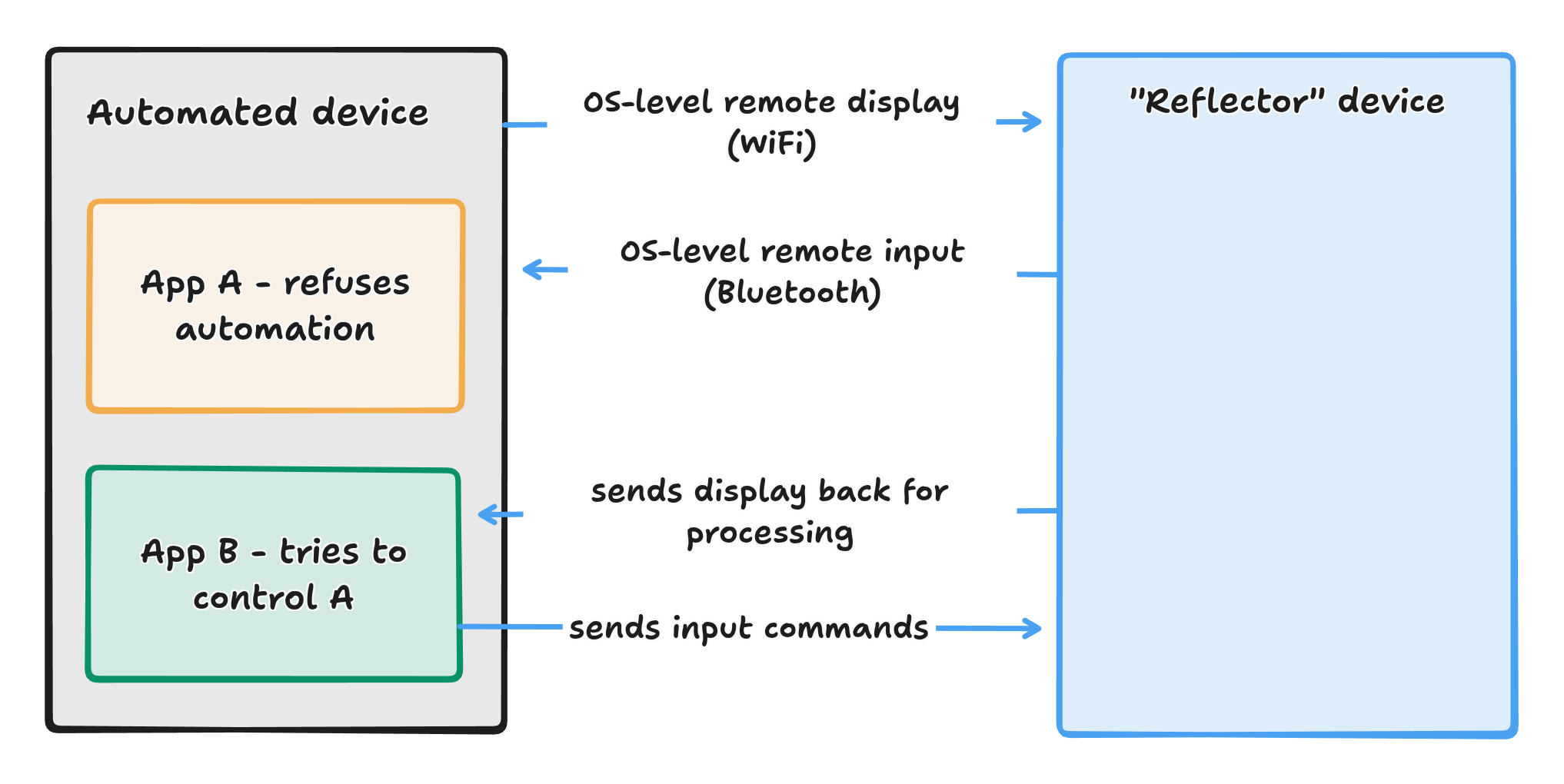
That would make a nice add-on functionality for virtualization tools such as QEMU.